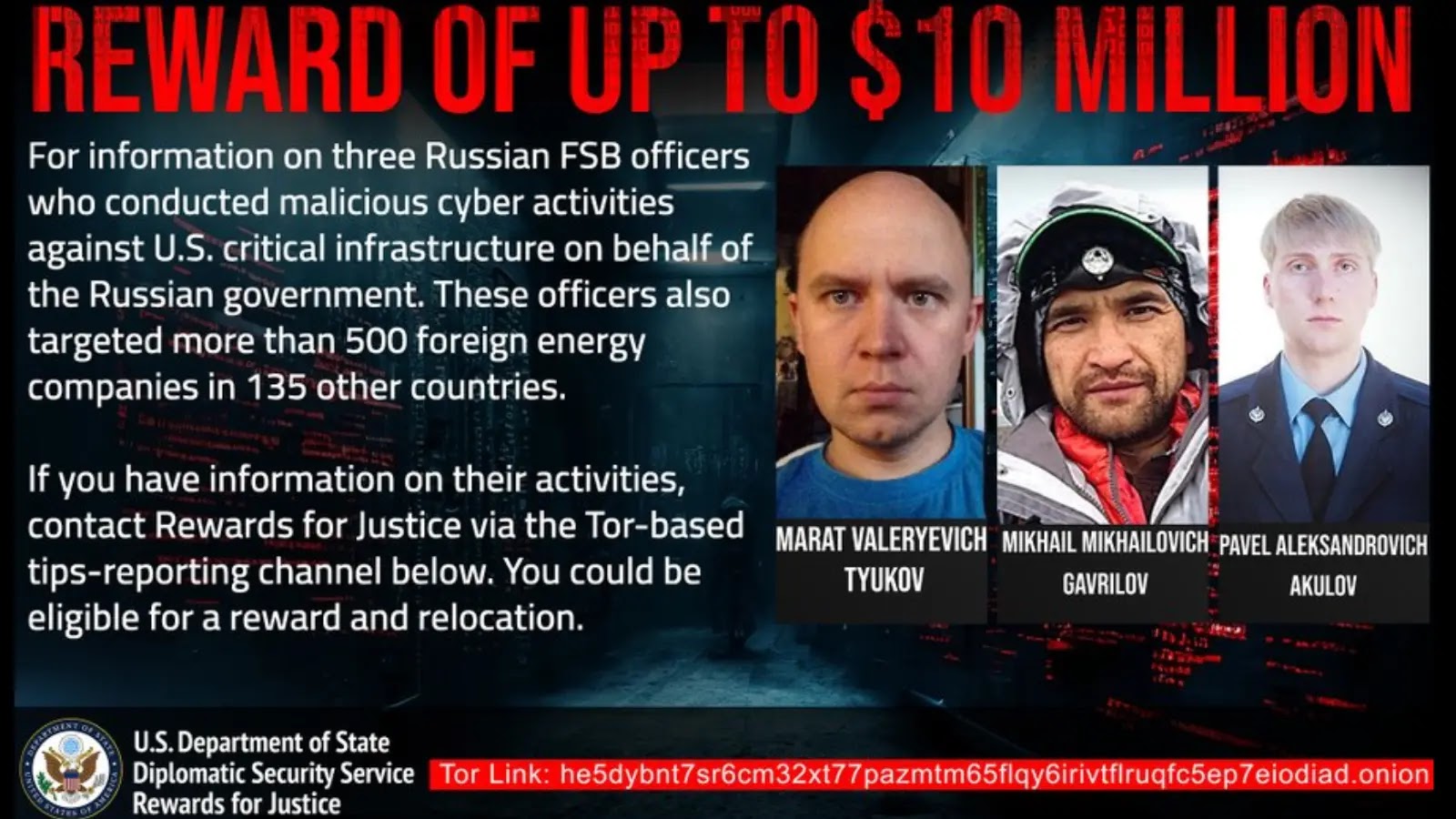
The United States government has announced a reward of up to $10 million for information leading to the identification or location of three Russian intelligence officers.
The bounty, offered through the Department of State’s Rewards for Justice program, targets members of the Russian Federal Security Service (FSB) accused of conducting widespread malicious cyber campaigns against U.S. critical infrastructure.
The announcement coincides with a new warning from the Federal Bureau of Investigation (FBI) detailing the activities of the FSB’s Center 16 unit.
The FBI has detected these state-sponsored hackers exploiting a known vulnerability in Cisco networking equipment to infiltrate computer networks globally.
The three officers identified in the reward posting are Marat Valeryevich Tyukov, Mikhail Mikhailovich Gavrilov, and Pavel Aleksandrovich Akulov.
In addition to their attacks on U.S. targets, the trio is accused of targeting over 500 foreign energy companies across 135 countries.
US Offers $10M Bounty For FSB Hackers
According to the FBI, the FSB cyber actors have been exploiting CVE-2018-0171, a critical vulnerability in the Cisco Smart Install (SMI) protocol.
The hackers specifically target end-of-life networking devices that are no longer receiving security updates.
By leveraging the Simple Network Management Protocol (SNMP) and the unpatched Cisco vulnerability, the group successfully collected configuration files from thousands of networking devices associated with U.S. entities in critical sectors.
Once inside the networks, the actors modified device configurations to create unauthorized backdoors.
This persistent access was then used to conduct detailed reconnaissance, with a particular focus on protocols and applications commonly used in industrial control systems (ICS).
US Offers $10M Bounty For FSB Hackers
This focus indicates a clear and dangerous interest in systems that manage essential services, such as power grids, water treatment plants, and manufacturing facilities.
This FSB hacking unit, known by various names in the cybersecurity community, including “Berserk Bear,” “Dragonfly,” and “Static Tundra,” has been active for over a decade.
The group has a long history of compromising networking devices worldwide, often by targeting equipment that uses legacy, unencrypted protocols like SMI and older versions of SNMP.
Their tradecraft includes deploying custom malware, such as the tool publicly identified as “SYNful Knock” in 2015, which was designed to compromise specific Cisco devices.
In response to this persistent threat, U.S. federal agencies and private sector partners have issued multiple alerts. Additionally, Cisco’s Talos intelligence group published its own analysis of the threat actor on August 20, 2025.
The Rewards for Justice program is now soliciting tips through a secure Tor-based channel, offering potential relocation in addition to the multimillion-dollar reward for information that helps disrupt these ongoing cyber operations.
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant Updates.