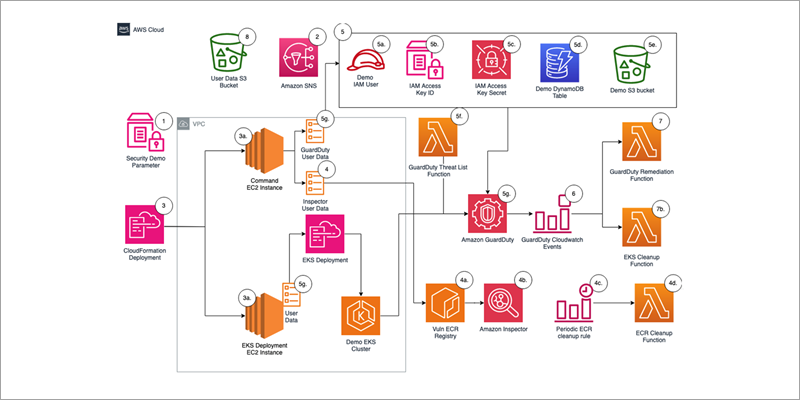
Continually reviewing your organization’s incident response capabilities can be challenging without a mechanism to create security findings with actual Amazon…
Author: sysops
In the evolving landscape of network security, safeguarding data as it exits your virtual environment is as crucial as protecting…
Security researchers have uncovered a critical vulnerability in the Linux kernel’s io_uring subsystem, which could allow attackers to gain full root access…
Network penetration testing plays a vital role in detecting vulnerabilities that can be exploited. The current method of performing pen…
GitLab has announced the release of updated versions for both its Community Edition (CE) and Enterprise Edition (EE), addressing critical…
Password spraying is a technique hackers often take advantage of because it enables them to gain unauthorized access to many…
Splunk Inc. has disclosed two significant vulnerabilities within its software suite, posing a considerable risk to organizations utilizing Splunk Enterprise…
Google patched seven vulnerabilities in the Chrome browser on Tuesday, including two zero-day exploits that were exploited at the Pwn2Own…
A security update released by ChatRTX on March 26th, 2024, addresses two vulnerabilities (CVE-2024-0082 and CVE-2024-0083) that could allow attackers…
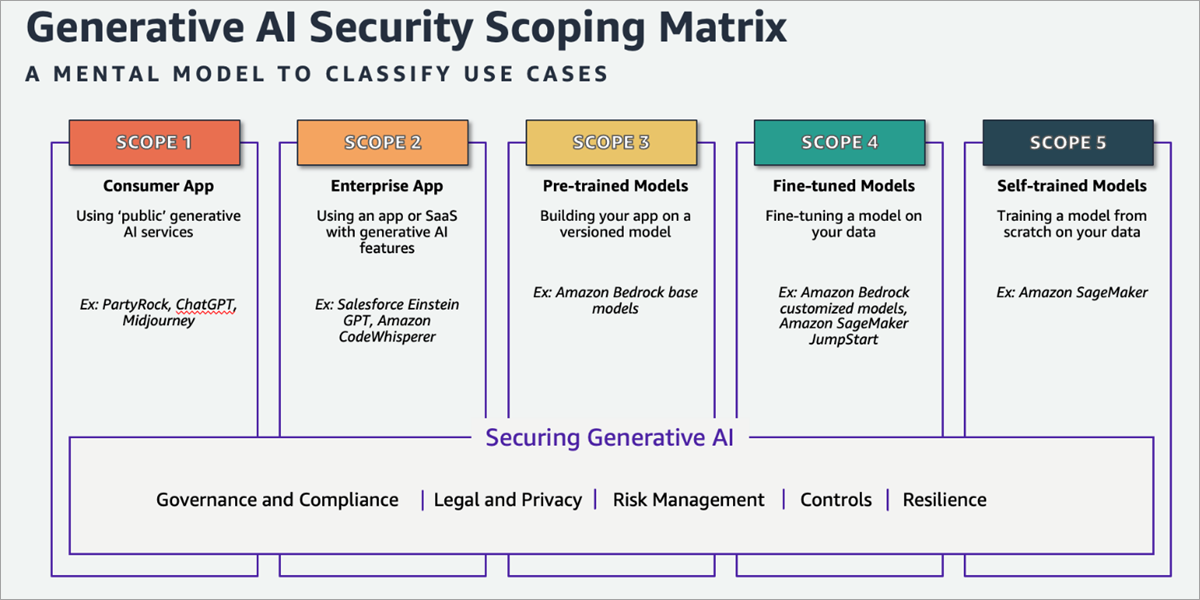
Generative artificial intelligence (AI) has captured the imagination of organizations and individuals around the world, and many have already adopted…