A proof-of-concept (PoC) exploit has been released for a critical unauthenticated, remote code execution vulnerability in Fortinet FortiSIEM, tracked as…
Author: sysops
VMware, a leading virtualization and cloud computing software provider, has issued patches for several critical and important vulnerabilities affecting its…
You might have security or compliance standards that prevent a database user from changing their own credentials and from having…
In a constantly evolving digital world, keeping the software supply chain and sensitive information secure is a priority for organizations…
A critical vulnerability, CVE-2024-4367, has been discovered in PDF.js, a widely used JavaScript-based PDF viewer maintained by Mozilla. The issue…
Amazon Web Services (AWS) successfully completed a special onboarding audit with no findings for ISO 9001:2015, 27001:2022, 27017:2015, 27018:2019, 27701:2019,…
Proxy-based dynamic application security testing was removed in GitLab 17.0 (May 16, 2024) and replaced with GitLab’s proprietary DAST tool…
.contains(context.jamfpolicy.risk) }; Choose Modify Verified Access group policy. The policy checks for claims received from the user trust provider (IAM…
All developers want to create secure and dependable software. They should feel proud to release their code with the full…
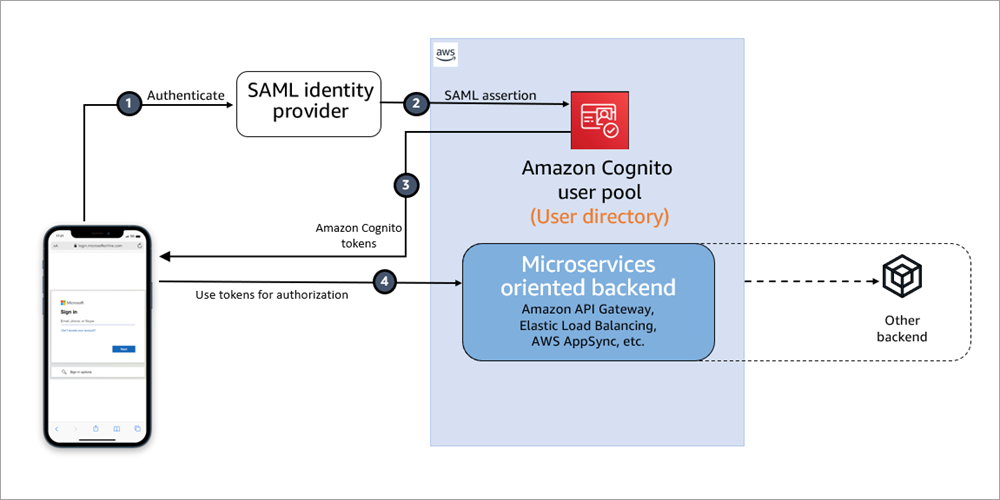
When an identity provider (IdP) serves multiple service providers (SPs), IdP-initiated single sign-on provides a consistent sign-in experience that allows…