Between crossovers – Do threat actors play dirty or desperate? In our dataset of over 11,000 victim organizations that have…
Author: sysops
Each day you build software there is another opportunity for security vulnerabilities to creep into production. So it is becoming…
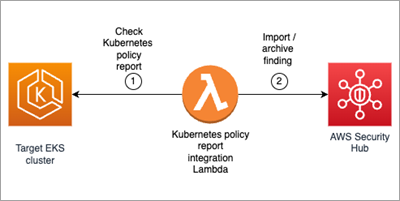
Using Kubernetes policy-as-code (PaC) solutions, administrators and security professionals can enforce organization policies to Kubernetes resources. There are several publicly…
French » Spanish » Amazon Web Services (AWS) is pleased to announce that a translated version of our 2023 ISO…
Google has announced a comprehensive update to the Chrome and Extended Stable channels. The latest release, version 124.0.6367.60/.61 for Windows…
An attacker with read-only or higher privileges on a Cisco Integrated Management Controller (IMC) can exploit a command injection vulnerability…
In a recent security advisory, Cisco disclosed a significant vulnerability in the implementation of the Simple Network Management Protocol (SNMP)…
Microsoft Security recently revealed a sophisticated cyber-attack campaign that targets Kubernetes clusters by exploiting newly discovered vulnerabilities in the OpenMetadata…
Our customers depend on Amazon Web Services (AWS) for their mission-critical applications and most sensitive data. Every day, the world’s…
Multiple Cloud Service providers like Google Cloud, AWS, and Azure have been discovered with a new vulnerability that has been…