CISA has issued an urgent warning regarding a critical path traversal vulnerability affecting D-Link DIR-859 routers that is being actively…
Category: Vulnerability
A newly disclosed vulnerability in Kubernetes has been identified that could allow compromised nodes to bypass critical authorization checks within…
A critical memory overflow vulnerability in NetScaler ADC and Gateway products could enable denial-of-service attacks. Exploits of this vulnerability have…
A severe security vulnerability has been discovered in Xiaomi’s interoperability application, potentially exposing millions of users to unauthorized device access. …
Summary 1. A high-severity flaw (CVE-2025-6218) in WinRAR allows attackers to execute arbitrary code by exploiting how the software handles…
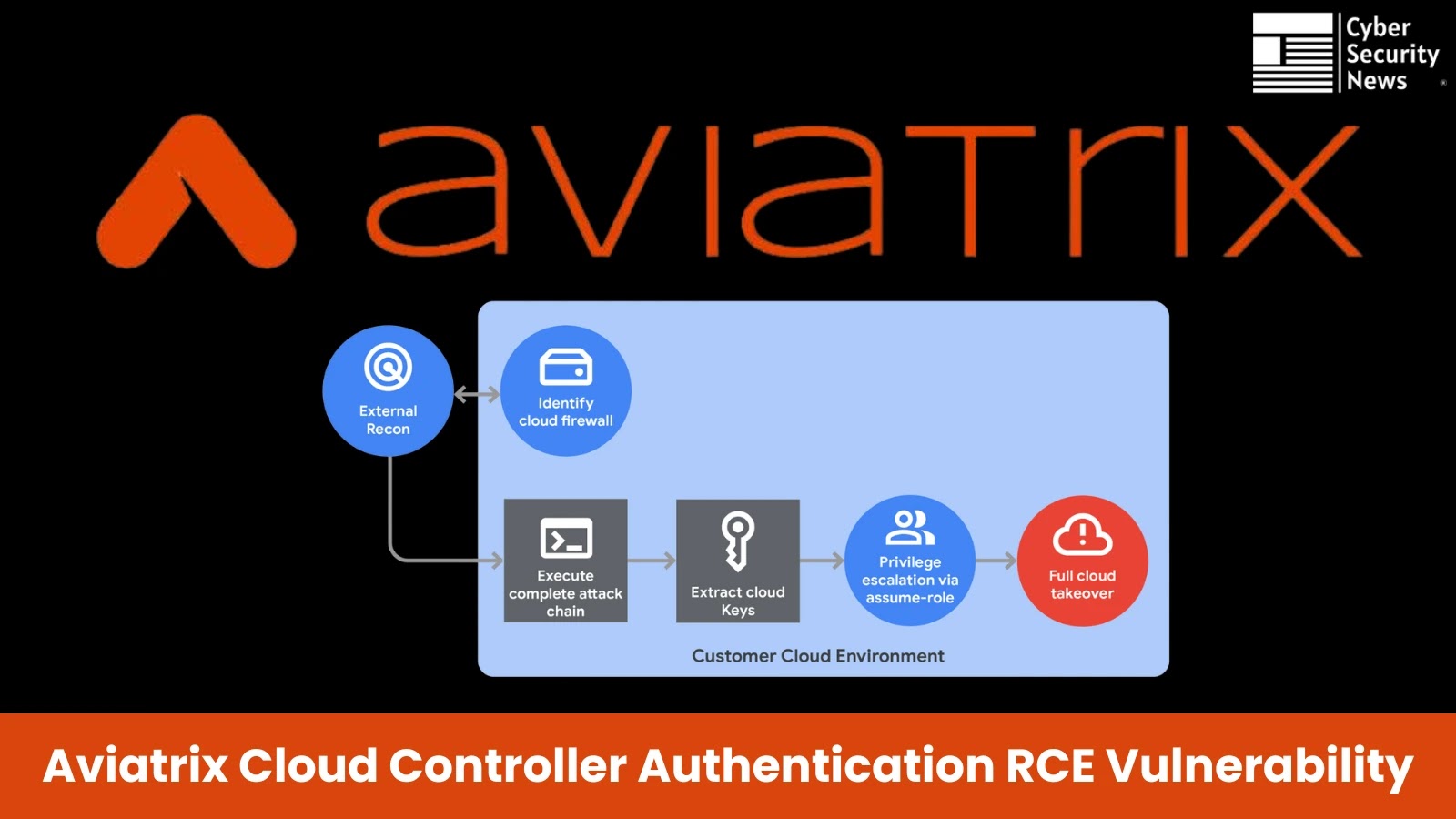
Two critical vulnerabilities in Aviatrix Controller, a Software-Defined Networking (SDN) utility that enables cloud connectivity across different vendors and regions. …
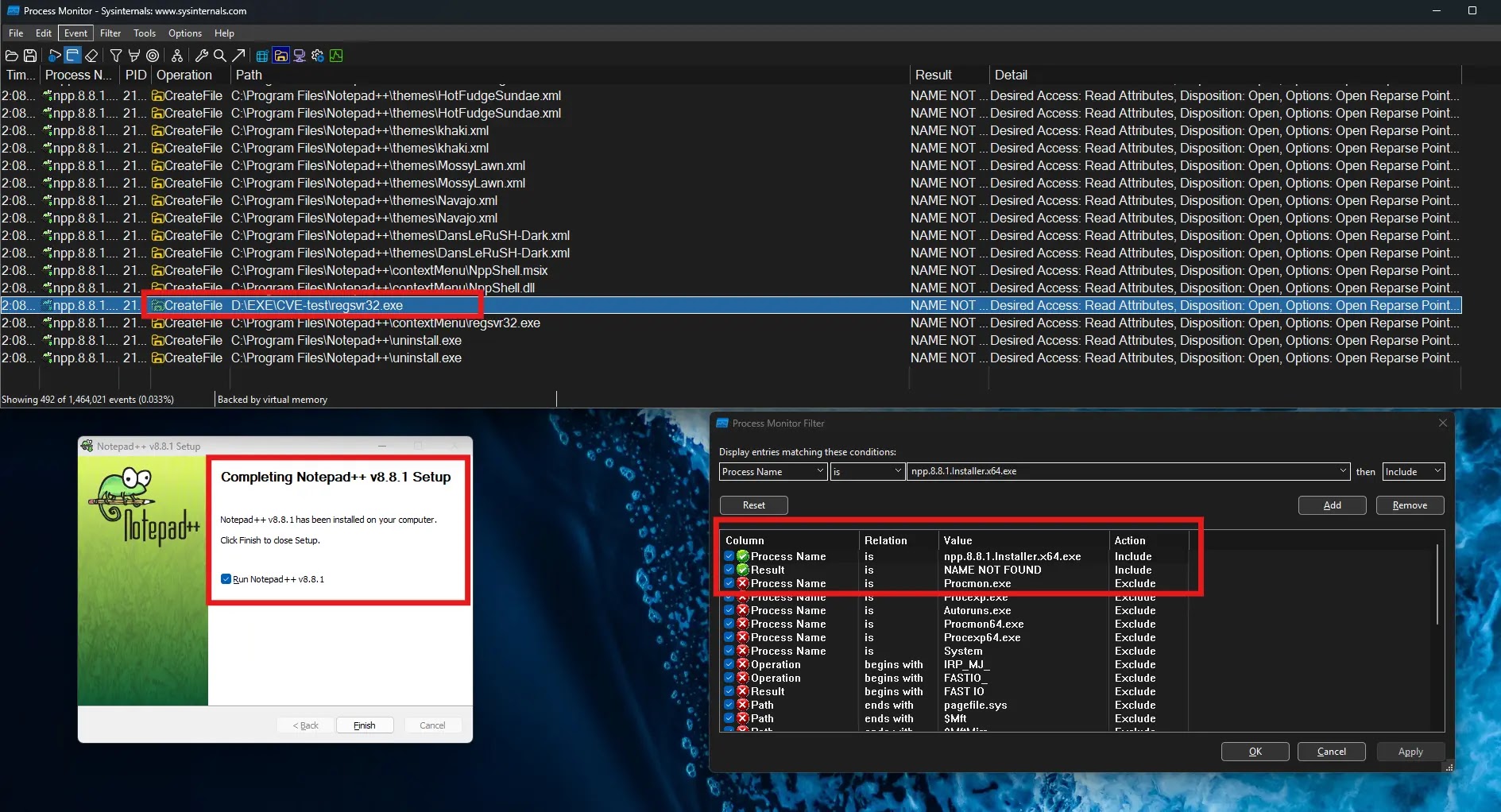
A severe privilege escalation vulnerability has been discovered in Notepad++ version 8.8.1, potentially exposing millions of users worldwide to complete…
Summary 1. CVE-2025-49825 allows attackers to remotely bypass Teleport’s authentication controls, affecting multiple versions of the secure access platform. 2. Teleport…
Summary 1. Harmful Objective Concealed: Attacker defines a harmful goal but starts with benign prompts. 2. Context Poisoning: Introduces subtle…
Summary 1. Meshtastic firmware above v2.5.0 has a severe security flaw allowing attackers to decrypt private messages. 2. Duplicate cryptographic…