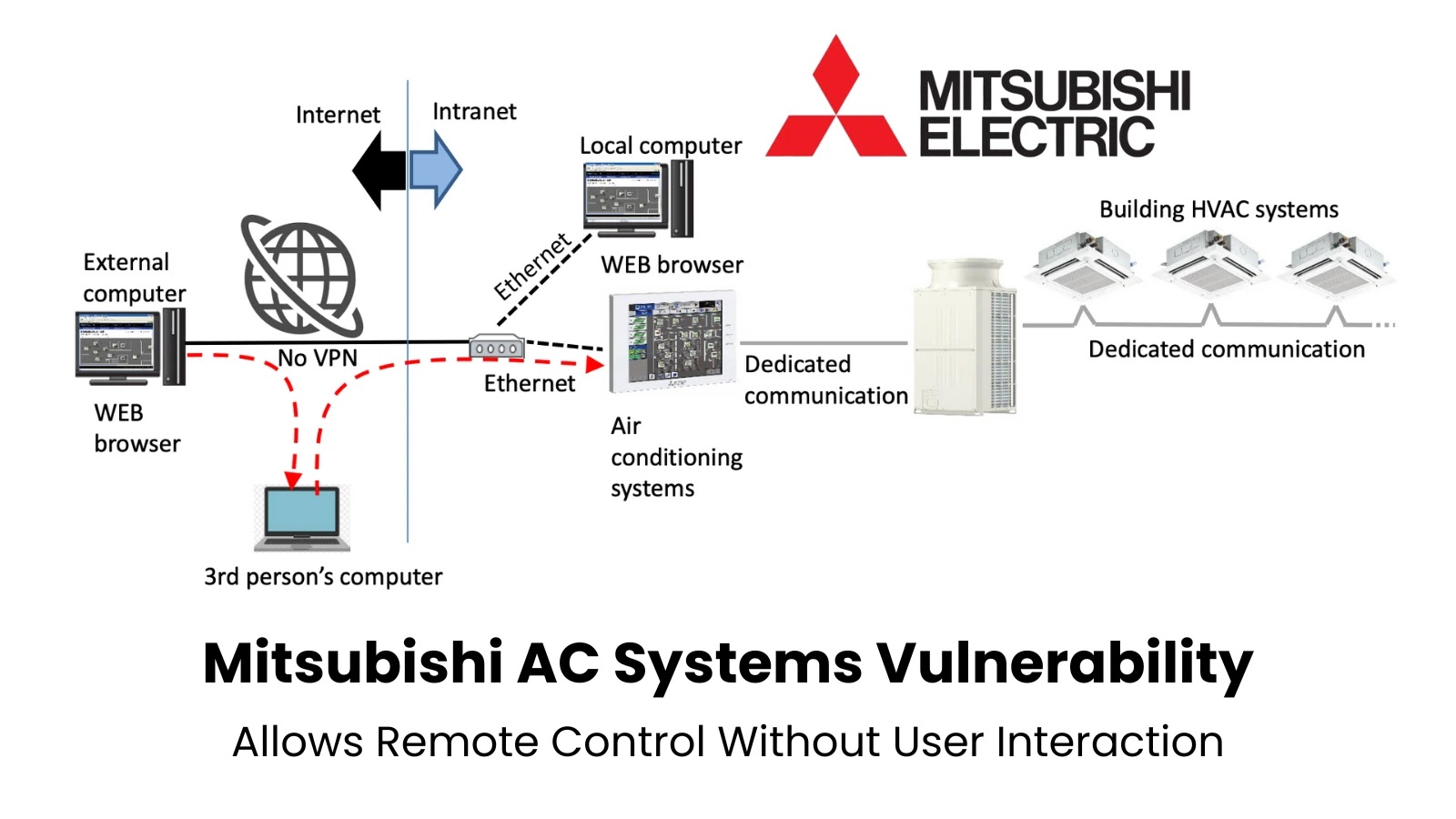
Mitsubishi Electric has disclosed a critical authentication bypass vulnerability affecting 27 different air conditioning system models, potentially allowing remote attackers to gain unauthorized control over building HVAC systems.
The vulnerability, tracked as CVE-2025-3699, carries a maximum CVSS score of 9.8, indicating its severe nature.
The vulnerability stems from a “Missing Authentication for Critical Function” weakness that enables attackers to bypass authentication mechanisms entirely.
Once exploited, malicious actors can illegally control air conditioning systems, access sensitive information, and even tamper with firmware using disclosed data.
The attack requires no user interaction and can be executed remotely over network connections, making it particularly dangerous.
Security researcher Mihály Csonka discovered and reported the vulnerability to Mitsubishi Electric, highlighting the collaborative effort between the security community and manufacturers to identify and address critical infrastructure vulnerabilities.
Widespread Impact Across Product Lines
The vulnerability affects a comprehensive range of Mitsubishi Electric air conditioning systems, including the G-50 series, GB-50 series, AE-200 and AE-50 series, EW-50 series, and various other models.
All affected systems running firmware versions 3.37 and prior (for G-series models), 9.12 and prior (for GB-24A), 3.21 and prior (for G-150AD and related models), 7.11 and prior (for EB-50GU models), 8.01 and prior (for AE/EW/TE/TW series), and 1.40 and prior (for CMS-RMD-J) are vulnerable to this attack vector.
The broad scope of affected products underscores the potential impact on commercial buildings, industrial facilities, and other environments where these systems are deployed for climate control and building automation.
Mitsubishi Electric outlined three system configuration scenarios in their advisory. The vulnerability poses the greatest risk in improperly configured environments where air conditioning systems are directly accessible from the internet without VPN protection.
In contrast, systems properly isolated within internal networks or protected by VPN routers face significantly reduced risk, as external attackers cannot directly reach the vulnerable services.
The company emphasized that their air conditioning systems are designed for use within secure intranet environments or networks protected by VPN infrastructure, highlighting the importance of proper network segmentation and access controls.
No Patches Available
Notably, Mitsubishi Electric announced there are no plans to release fixed firmware versions for most affected products. However, the company is preparing improved versions for select models in the AE-200, AE-50, EW-50, TE-200, TE-50, and TW-50A series to address this vulnerability.
Complete Affected Systems Table
SeriesModelAffected VersionCVECVSS ScoreAE SeriesAE-200AVer.8.01 and prior1CVE-2025-36999.8AE SeriesAE-200EVer.8.01 and prior1CVE-2025-36999.8AE SeriesAE-200JVer.8.01 and prior1CVE-2025-36999.8AE SeriesAE-50AVer.8.01 and prior1CVE-2025-36999.8AE SeriesAE-50EVer.8.01 and prior1CVE-2025-36999.8AE SeriesAE-50JVer.8.01 and prior1CVE-2025-36999.8CMS SeriesCMS-RMD-JVer.1.40 and prior1CVE-2025-36999.8EB-50GU SeriesEB-50GU-AVer.7.11 and prior1CVE-2025-36999.8EB-50GU SeriesEB-50GU-JVer.7.11 and prior1CVE-2025-36999.8EW-50 SeriesEW-50AVer.8.01 and prior1CVE-2025-36999.8EW-50 SeriesEW-50EVer.8.01 and prior1CVE-2025-36999.8EW-50 SeriesEW-50JVer.8.01 and prior1CVE-2025-36999.8G-150/AG-150/GB-50AD SeriesAG-150A-AVer.3.21 and prior1CVE-2025-36999.8G-150/AG-150/GB-50AD SeriesAG-150A-JVer.3.21 and prior1CVE-2025-36999.8G-150/AG-150/GB-50AD SeriesG-150ADVer.3.21 and prior1CVE-2025-36999.8G-150/AG-150/GB-50AD SeriesGB-50ADVer.3.21 and prior1CVE-2025-36999.8G-150/AG-150/GB-50AD SeriesGB-50ADA-AVer.3.21 and prior1CVE-2025-36999.8G-150/AG-150/GB-50AD SeriesGB-50ADA-JVer.3.21 and prior1CVE-2025-36999.8G-50/GB-50 SeriesG-50Ver.3.37 and prior1CVE-2025-36999.8G-50/GB-50 SeriesG-50-WVer.3.37 and prior1CVE-2025-36999.8G-50/GB-50 SeriesG-50AVer.3.37 and prior1CVE-2025-36999.8G-50/GB-50 SeriesGB-50Ver.3.37 and prior1CVE-2025-36999.8G-50/GB-50 SeriesGB-50AVer.3.37 and prior1CVE-2025-36999.8GB-24A SeriesGB-24AVer.9.12 and prior1CVE-2025-36999.8TE SeriesTE-200AVer.8.01 and prior1CVE-2025-36999.8TE SeriesTE-50AVer.8.01 and prior1CVE-2025-36999.8TW SeriesTW-50AVer.8.01 and prior1CVE-2025-36999.8
For immediate protection, Mitsubishi Electric recommends implementing several mitigation strategies: restricting network access from untrusted sources, limiting physical access to systems and connected infrastructure, and maintaining updated antivirus software and web browsers on computers used to manage these systems.
This disclosure highlights the growing security challenges facing building automation and IoT infrastructure. As critical systems become increasingly connected, the potential for remote exploitation grows, emphasizing the need for robust security practices in industrial and commercial environments.
Organizations using affected Mitsubishi Electric air conditioning systems should immediately assess their network configurations and implement recommended security measures to prevent potential exploitation of this critical vulnerability.
Investigate live malware behavior, trace every step of an attack, and make faster, smarter security decisions -> Try ANY.RUN now